Categories: Castelia
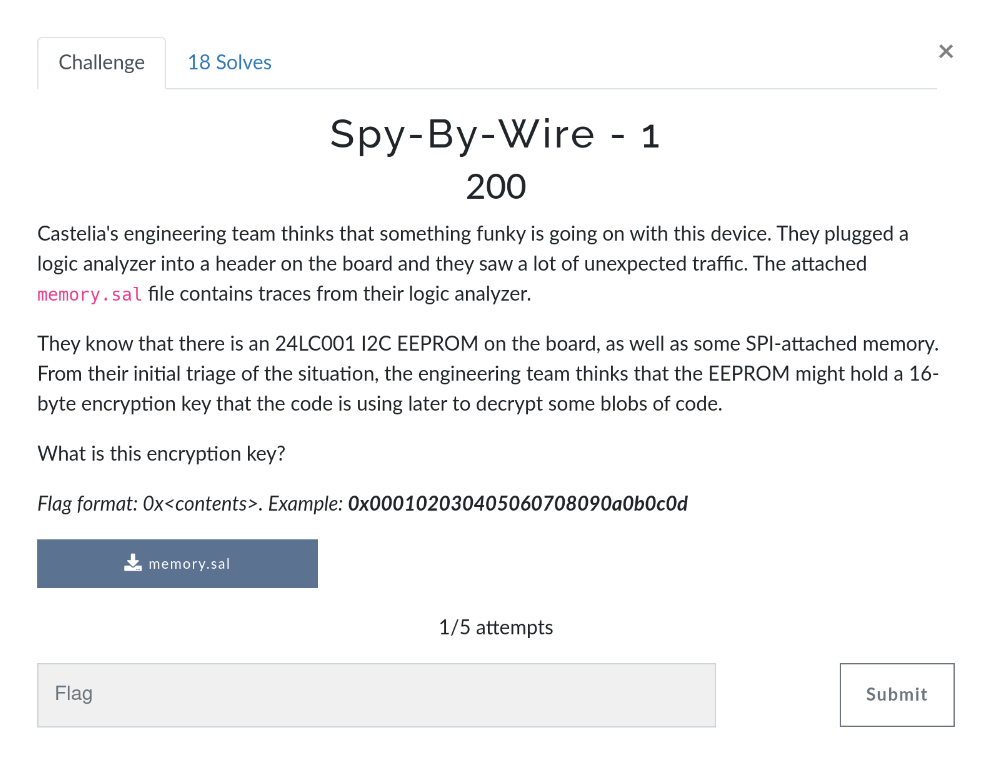
At first this challenge was hard for me to understand because I had no idea about Saleae. But I wanted to solve this challenge and learn something. Firstly to understand the challenge, what do it want to say. So in this project, we are tasked with examining data traces captured by a logic analyzer to find a 16-byte encryption key stored in an I2C EEPROM. The provided file contains traces for both I2C and SPI protocols. The encryption key stored in the EEPROM plays a critical role in the device’s operation, and it is suspected that this key is later used to decrypt encrypted data.
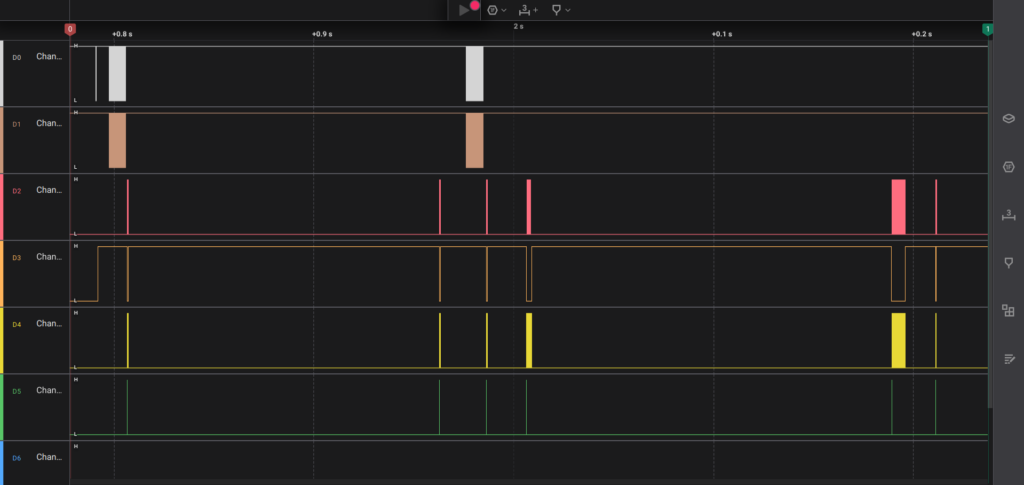
memory.sal file in Logic Analyzer At this stage we need more information about filtering in I2C and Logic Analyzer. We can learn how to do filtering for I2C protocol using Logic Analyzer from Saleae official website.
I2C is a protocol used for low-speed and short-distance communication between integrated circuits. Data exchange over I2C is carried out using two main lines: SCL (Serial Clock Line) and SDA (Serial Data Line). EEPROM devices like the 24LC001 use this protocol for reading and writing data. Typically, these devices follow a master-slave architecture and have a specific address.
SCL is the periodic clock signal. SDA transmits the data and should change when SCL is low. Based on this information, SCL is probably Channel 1 and SDA is Channel 0. We filtered on Logic Analyzer and was to find the 16-byte encryption key stored in an I2C EEPROM using data captured by a logic analyzer.
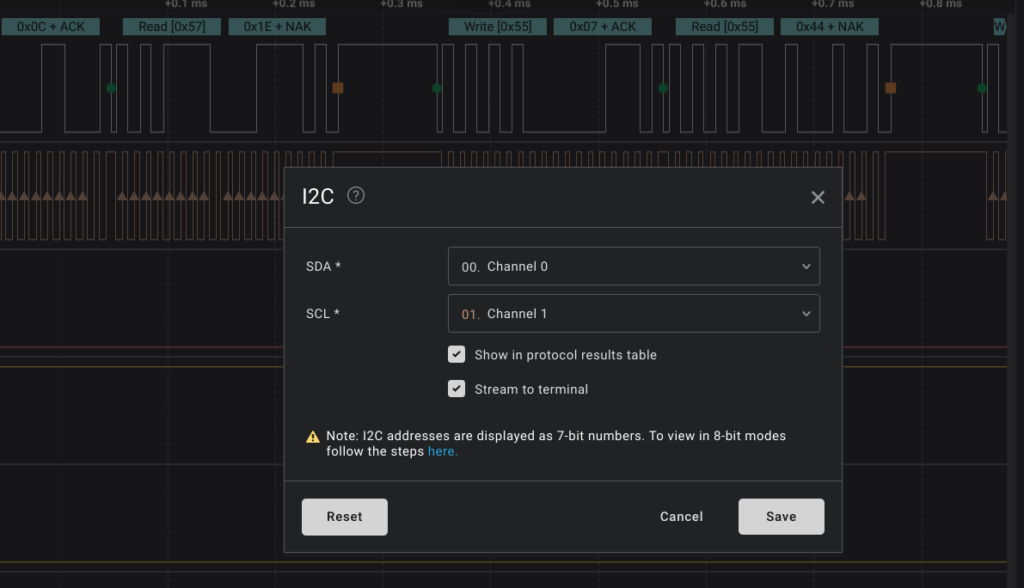
As you can see, we were able to extract all I2C data in “.csv” format or we can also separate it in Excel by simply copy-pasting the data from the terminal into Excel.
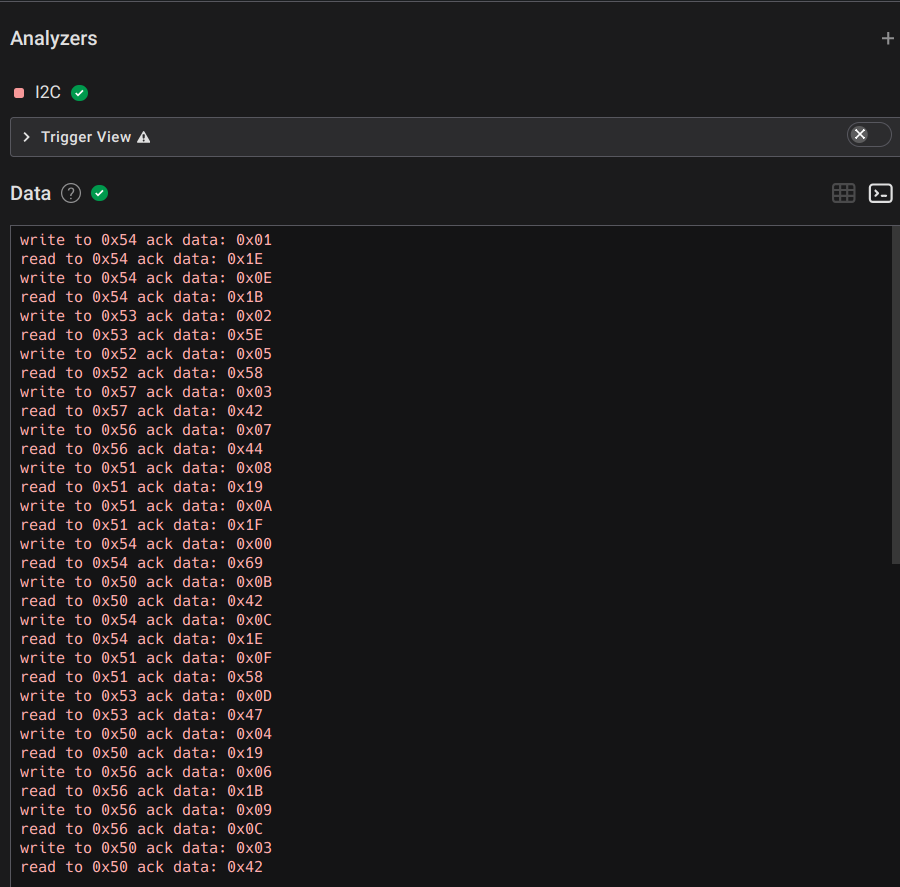
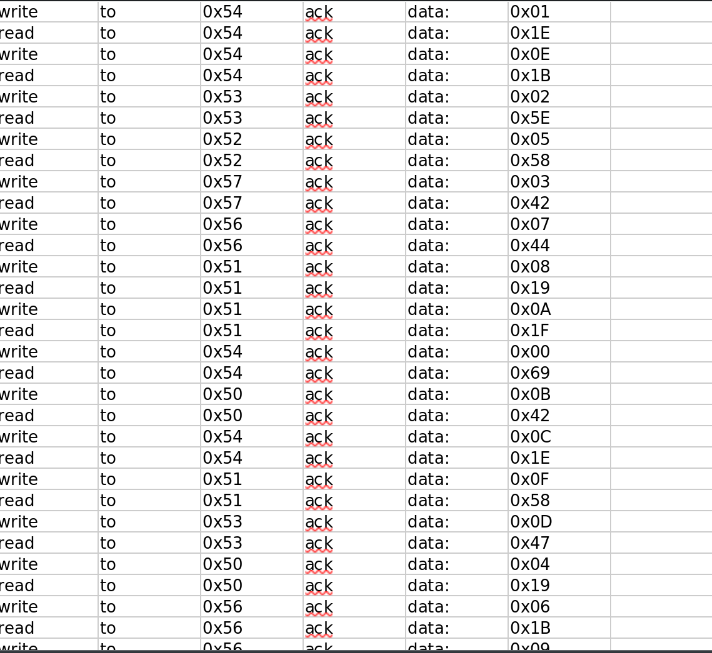
If you follow the read and write information, you will see that they are not in order. We can understand that a 16-byte encryption key in this non-sequential data. Let’s try to separate and sort the data in the read and write information. While sorting, we also see that the data repeats itself after a 16-byte section
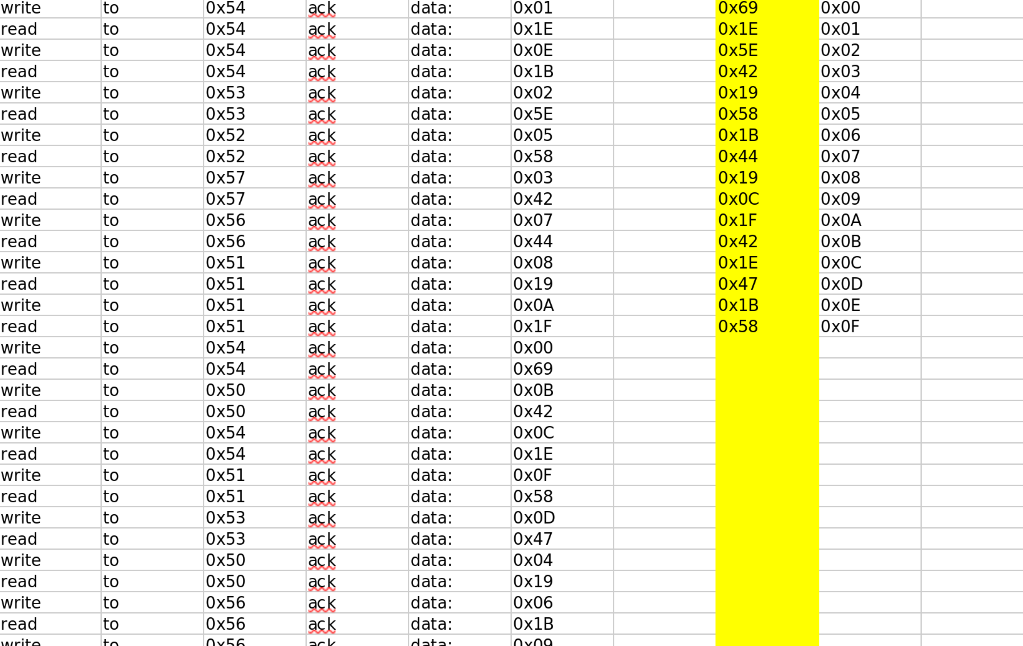
Finally we found the part of the data in this non-consecutive file that has the 16-byte encryption key and we arrange it according to the flag format.
Flag: 0x691E5E4219581B44190C1F421E471B58

