Challange 1: frog
First thing first, this is my first flare-on ctf challenge ever. That was very exciting and challenging experience for me. And, this write-up serious will be answer of “How to begin for Reverse Engineering” question.
If you wanna try this challenge, here is the link below;
https://github.com/sevkaz/flare-on11/tree/main/Challenge-1
So, if you open challenge file, you will see a PyGame program that comes packaged with a README.txt file for launching instructions.
When we follow the instructions and run the PyGame-based frog.py file, we will see this;
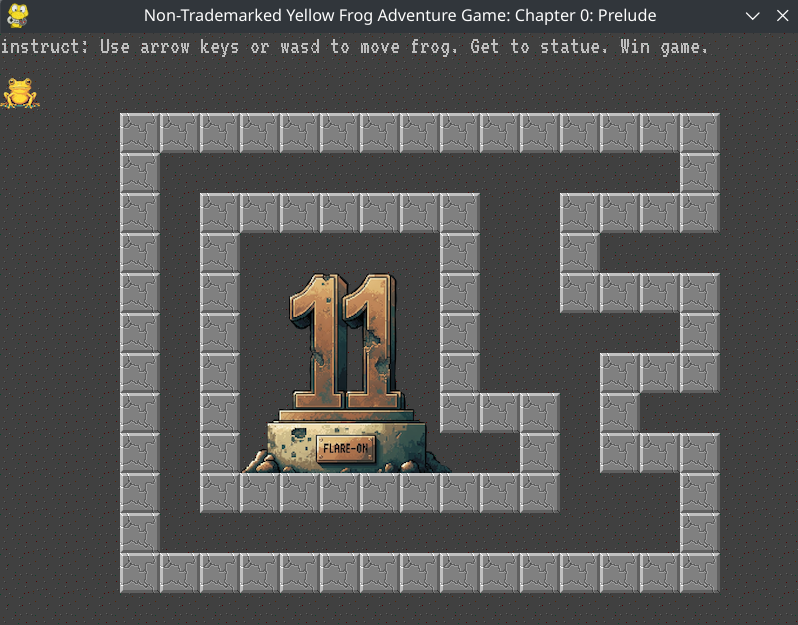
You can solve in two ways;
First of all it doesn’t require any knowledge about Reverse Engineering. You can try your luck and solve it manually by just skipping a few blocks.
Secondly, we will do code analysis and that is Reverse Engineering.
Code Analysis
The key part of the challenge was reverse engineering the provided Python source code. By inspecting the code, we found:
- Victory Tile:
victory_tile = pygame.Vector2(10, 10)This indicated that the flag would be generated when the frog reached the coordinate (10, 10).
- Flag Generation Function: Upon further exploration, we uncovered the
GenerateFlagTextfunction:
def GenerateFlagText(x, y):
key = x + y * 20
encoded = "\xa5\xb7\xbe\xb1\xbd\xbf\xb7\x8d\xa6\xbd\x8d\xe3\xe3\x92\xb4\xbe\xb3\xa0\xb7\xff\xbd\xbc\xfc\xb1\xbd\xbf"
return ''.join([chr(ord(c) ^ key) for c in encoded])Here for flag:
keywas derived from the frog’s final position.encodedwas a string of bytes XORed with the key to produce the flag.
Reconstructing the Flag
Rather than playing the game manually, we used the following Python code to compute the flag directly:
def GenerateFlagText(x, y):
key = x + y * 20
encoded = "\xa5\xb7\xbe\xb1\xbd\xbf\xb7\x8d\xa6\xbd\x8d\xe3\xe3\x92\xb4\xbe\xb3\xa0\xb7\xff\xbd\xbc\xfc\xb1\xbd\xbf"
return ''.join([chr(ord(c) ^ key) for c in encoded])
# Simulate the frog reaching the victory tile
x = 10
y = 10
flag = GenerateFlagText(x, y)
print(flag)
And, The way with Reverse Engineering is just about read correctly python code and understand “How to leverage XOR operations to decrypt encoded data”. So, We were able to solve the logic of this game by interacting directly with the source code.
Finally, the output and flag:
[email protected]
